





When two images are superimposed,a new different pattern appears.This kind of pattern is called‘moirépattern’.Based on this phenomenon,Muñoz-Rodríguez and Rodríguez-Vera[1]proposed a novel image encryption based on moirépattern performed by computational algorithms.A certain reference fringe pattern is used to encrypta secret image.The secret image can be reconstructed by simple computation with the same parameters.Ragulskis and Aleksa[2,3]improved this algorithm and proposed an image hiding algorithm based on time-averagingmoiré.The secret image can be reconstructed by naked eye when a time-averaging moirépattern is harmonically oscillated in a predefined direction.Based on their algorithm,Ragulskis and Aleksa[4]proposed an image hiding algorithm based on time-averaged fringes produced by non-harmonic oscillations.Ragulskis et al.[5]proposed an image hiding algorithm based on circularmoire fringes.Sakyte et al.[6]proposed an image hiding algorithm based on near-optimal moirégratings.Palivonaite et al.[7]proposed an image hiding algorithm in time-averaged deformable moirégratings.Petrauskiene et al.[8]proposed a dynamic visual cryptography based on chaotic oscillations.In these improved algorithms[2-8],the basic generating equations and parameters are almost the same as those in[1].Experimental results of[1-8]did not give related parameters,nevertheless,we know that the reconstruction quality may be different when we use the same algorithm with different parameters(about this point,see Fig.1 of section 2).So,it is worthwhile to study the relationship among reconstruction quality and parameters of generating equations.
This paper is organized as follows.Section 2 reviews the algorithm proposed by Muñoz-Rodríguez and Rodríguez-Vera and discusses two superimposition models for grey-scale image.In Section 3,we propose a method to calculate the reconstruction quality and give its relationship with parameters of generating equations.Then in Section 4,we use the proposed method to com-pare and discuss the reconstruction quality in another image hiding algorithm based on moirépattern.Section 5 concludes the paper.
Muñoz-Rodríguez and Rodriguez-Vera[1]proposed an image encryption based onmoirépattern performed by computational algorithms.It is one of the most typical image hiding algorithms based onmoire pattern.A certain reference fringe pattern is used to encrypta secret image.The secret image can be reconstructed by simple computation with the same parameters.
This algorithm is reviewed as follows.
TABLE 1 ALGORITHM PROPOSED BY MUÑOZ-RODRíGUEZ AND RODRíGUEZ-VERA

In this algorithm, I R ( x , y )denotes the reference fringe pattern and it can be obtained as
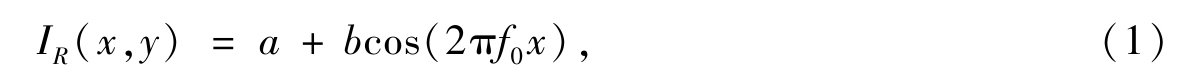
where a and b are the background intensity and contrast of the fringe pattern,respectively,and f 0 is the fundamental frequency.
I D ( x , y )denotes the encrypted image and it is described as
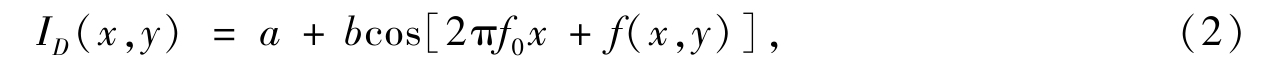
where the intensity function f ( x , y )stands for the secret image.
M p ( x , y )denotes themoirépattern and it is described by
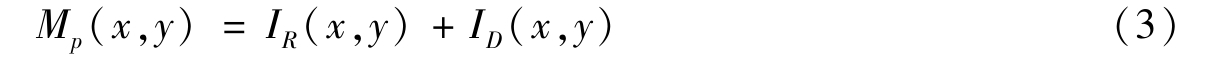
According to(1)and(2),the value of the pixel is between a - b and a + b .So we can let a , b >0.In image processing,a white pixel is represented as a 0,and a black pixel is represented as a 1.In general,we can let a =0.5 and b =0.5,and then the value of the pixel is between 0 and 1.We can let M p ( x , y )=1 when M p ( x , y ) =I R ( x , y ) +I D ( x , y )>1.
In printing and image processing,Multiply mode[10]is commonly used to obtain moiré pattern when superimposing two grey-scale images.If a white pixel is represented as a 0 and a black pixel is represented as a 1,themoire pattern is described by
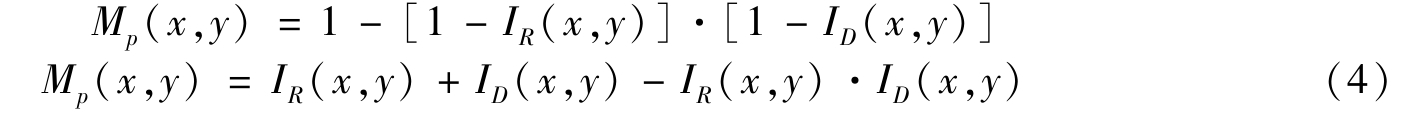
We use the secret image in[1]as experimental image.Using the above algorithmswith different f 0 ,partial experimental results are shown in Fig 1.
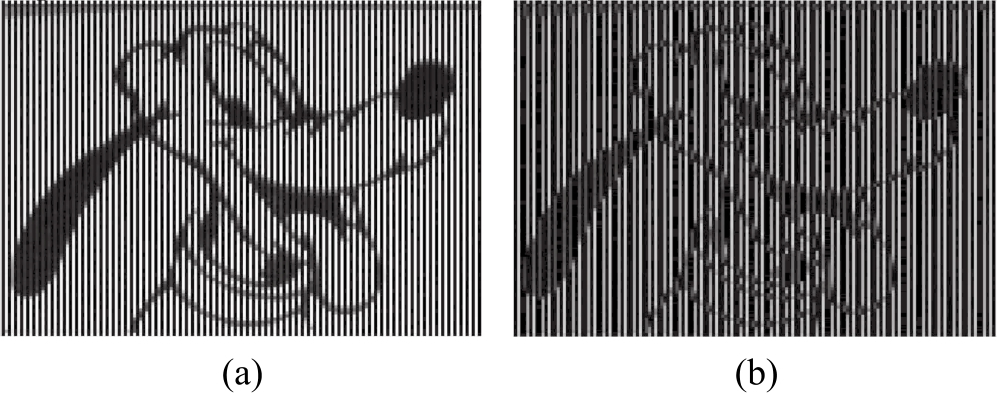
Figure 1.Reconstructed images w ith different f 0 :(a) f 0 = 0.5;(b) f 0 = 0.4
From the experimental results above we can see that encrypted imageswith different parameters can reconstruct the secret image correctly,butwe cannot tell the difference between two similar reconstructed images like Fig.1(a)and Fig.1(b).
In section 2,we note the fact thatwhen difference between two parameters is very small,it is difficult to distinguish one reconstructed image from another by human vision,such as Fig.1(a)and Fig.1(b).Traditionally,image quality has been evaluated by human subjects.This method,though reliable,is expensive and too slow for real-world applications.So computational models that can automatically predict perceptual image quality are needed[9].Refer to the definition ofWang et al.[11,12]'s average contrast,next we give a definition of‘average contrast’in image hiding algorithms based on moirépattern.
Definition 1
.
For a secret image with a grey-levels
,
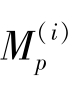 denotes themoirépattern of the ithgrey-level area in it
.
The average grey-level of
denotes themoirépattern of the ithgrey-level area in it
.
The average grey-level of
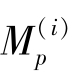 is
is
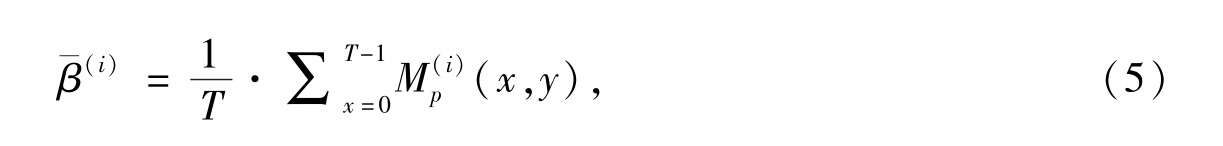
where T is theminimum period of the generating equations . When T is big enough , then
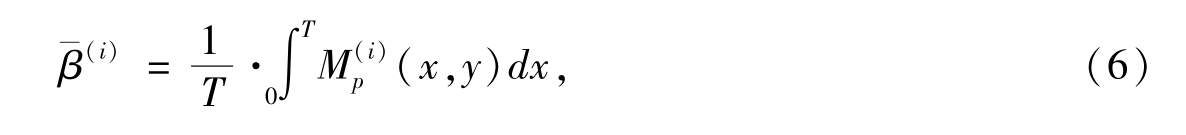
Average contrast betwenn the ith and the ( i +1) the average grey-levels is
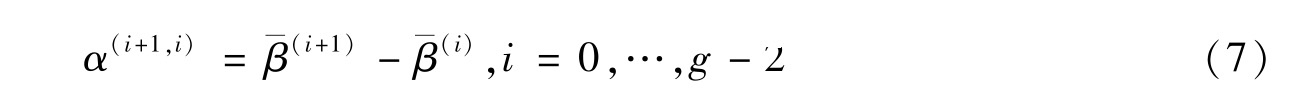
Using Definition 1 ,we give the analysis about parameter f 0 and reconstruction quality below.
Lemma 1
.Letf
0
∈
R
,
then there are integers p and q
,
with q
≠0,
such that f
0
=
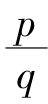 .
Then
theminimum period of the generating equations is T=q
.
.
Then
theminimum period of the generating equations is T=q
.
Proof : We prove this lemma by two steps.
(i)According to(2),
I
D
(
x+q
,
y
)
=a+b
cos[ 2π·
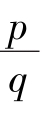 ·(
x+q
)
+f
(
x
,
y
)]
=a+b
cos[ 2π
p+
2π·
·(
x+q
)
+f
(
x
,
y
)]
=a+b
cos[ 2π
p+
2π·
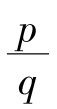 ·
x+f
(
x
,
y
)]
=a+b
cos[ 2π·
·
x+f
(
x
,
y
)]
=a+b
cos[ 2π·
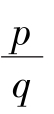 ·
x+f
(
x
,
y
)]
=I
(
x
,
y
).
D
·
x+f
(
x
,
y
)]
=I
(
x
,
y
).
D
Let f ( x , y ) = 0,then I R ( x , y ) =I R ( x+q , y ).So q is a period of the generating equations.
(ii)Proof by contradiction:If there exists
q'<q
and
I
D
(
x
,
y
)
=I
D
(
x+q'
,
y
)for any given
x
,then
I
D
(
x+q′
,
y
)
=a+b
cos[ 2π·
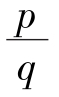 ·(
x+q′
)
+f
(
x
,
y
)]
=a+b
cos
·(
x+q′
)
+f
(
x
,
y
)]
=a+b
cos
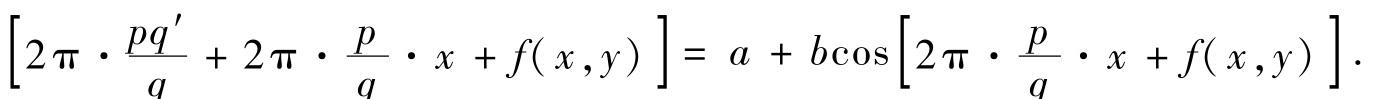
So
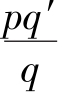 is an integer,namely
is an integer,namely
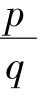 is not a simplest fraction.It is contradictwith our precondition.So
q
is theminimum period of the generating equations.
is not a simplest fraction.It is contradictwith our precondition.So
q
is theminimum period of the generating equations.
Theorem 1.
Let
f
0
=
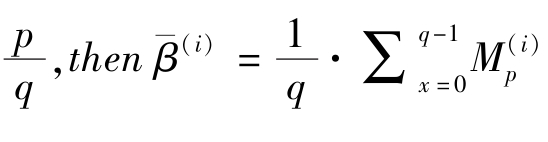 (
x
,
y
)
=
(
x
,
y
)
=
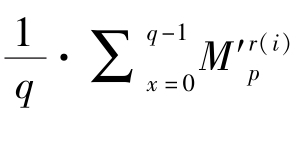 (
x
,
y
),
where
(
x
,
y
),
where
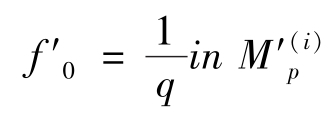 (
x
,
y
).
(
x
,
y
).
Proof
:We need to prove that
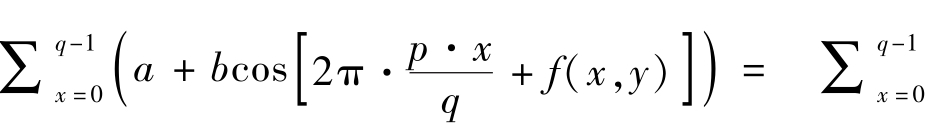
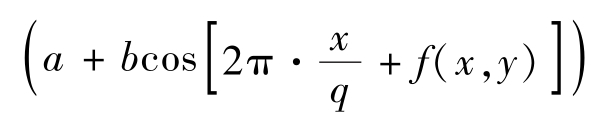 .As
p
,
q
,
x
and
y
are all integers,if
p
·
x
≤
q-
1,there exists
k=p
·
x
in the right formula than
.As
p
,
q
,
x
and
y
are all integers,if
p
·
x
≤
q-
1,there exists
k=p
·
x
in the right formula than
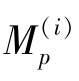 (
k
,
y
).
Ifp
·
x>q-
1,namely
p
·
x
≥
q
,then
a+b
cos[ 2π·
(
k
,
y
).
Ifp
·
x>q-
1,namely
p
·
x
≥
q
,then
a+b
cos[ 2π·
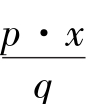 +f
(
x
,
y
)]
=a+b
cos
+f
(
x
,
y
)]
=a+b
cos
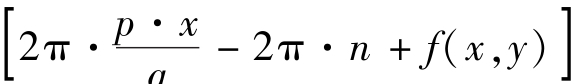 =a+b
cos[2π·
=a+b
cos[2π·
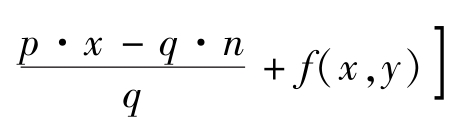 .There exists an integer
n
and(
p
·
x-q
·
n
)∈[0,
q-
1].So there also exists
k′=
(
p
·
x-q
·
n
)in the right formula that
.There exists an integer
n
and(
p
·
x-q
·
n
)∈[0,
q-
1].So there also exists
k′=
(
p
·
x-q
·
n
)in the right formula that
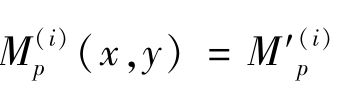 (
k′
,
y
).According to Lemma 1,theminimum period of the generating equations is
T
=
q
,so items in the left formula will be one-onemapping to items in the right formula,thus the theorem is proven.
(
k′
,
y
).According to Lemma 1,theminimum period of the generating equations is
T
=
q
,so items in the left formula will be one-onemapping to items in the right formula,thus the theorem is proven.
Ragulskis and Aleksa[2]analyzed the algorithm in[1].The generating equations can be expressed as
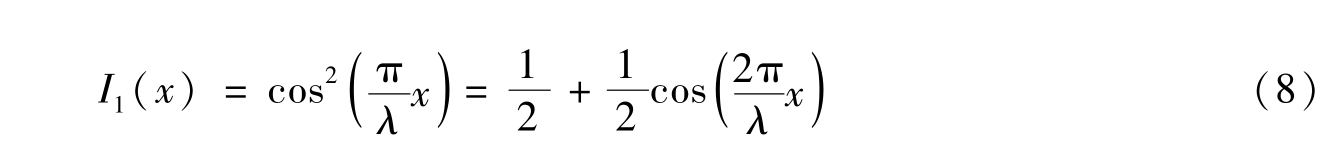
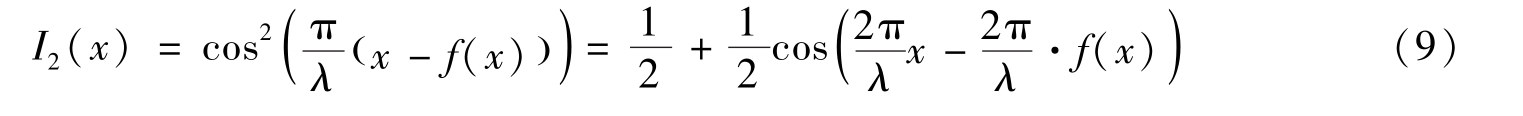
They proved the following conclusion and we use it as a lemma.
Lemma 2 [ 2] . f ( x , y ) should bemapped into 0 and π.
Proof
:
Let
a
=0.5 and
b
=0.5,then(1)is same as(8)and(2)is same as(9).We learn from[2]that0≤
f
(
x
)≤
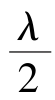 ,so
f
(
x
,
y
)
=
,so
f
(
x
,
y
)
=
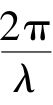 ·
f
(
x
)∈[0,π].
·
f
(
x
)∈[0,π].
Theorem 2.
Let f
0
=
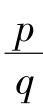 ,
when T is big enough
,
then the expected value of
,
when T is big enough
,
then the expected value of
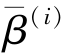 is
is
(
i
)
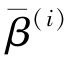 =
1
-
=
1
-
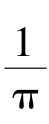 ·sin
·sin
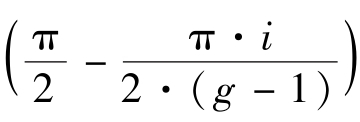 by Sum mode
,
by Sum mode
,
(ii)
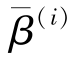 =
=
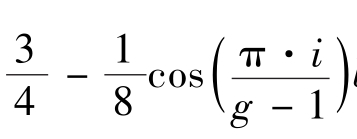 by Multiplymode
.
by Multiplymode
.
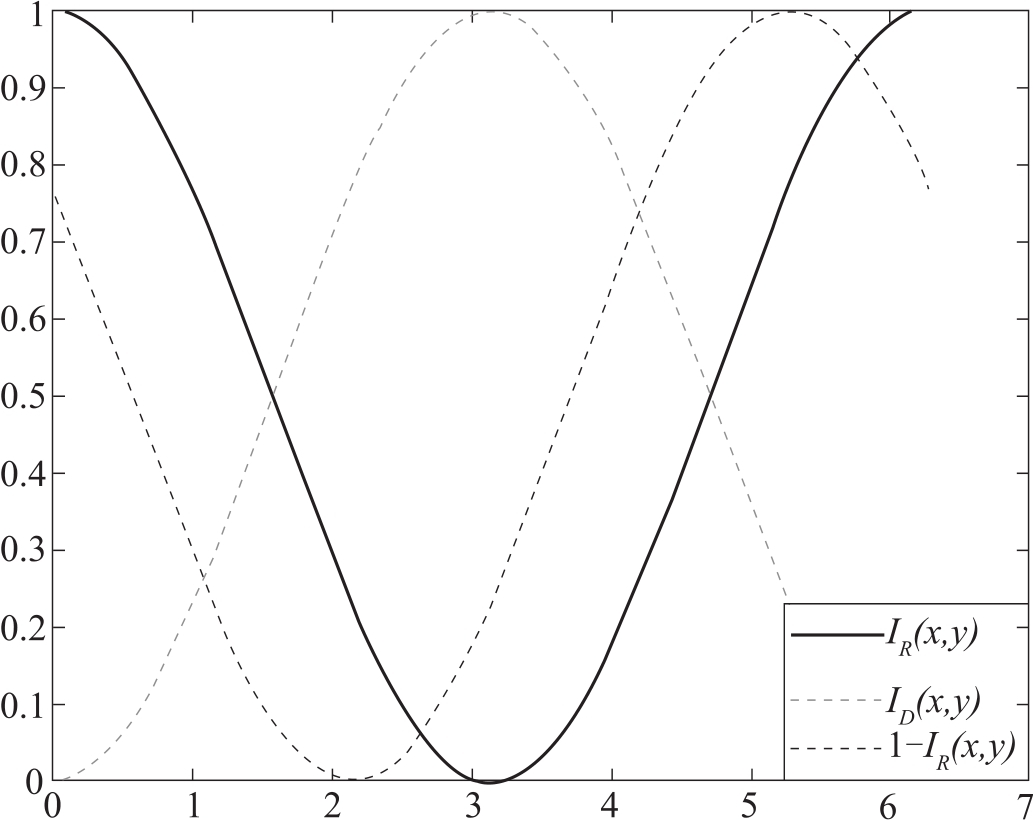
Figure 2 Equation image of I R , I D and 1- I R
Proof
:
According to Theorem 1,if
f
0
=
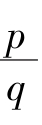 ,we can use
,we can use
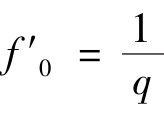 to calculate the average grey-level.The value of the ith grey-level
f
(
i
)
(
x
,
y
)can bemapped into
to calculate the average grey-level.The value of the ith grey-level
f
(
i
)
(
x
,
y
)can bemapped into
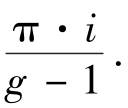
To prove(i),when we superimpose two grey-scale images by Sum mode,themoirépattern is described by
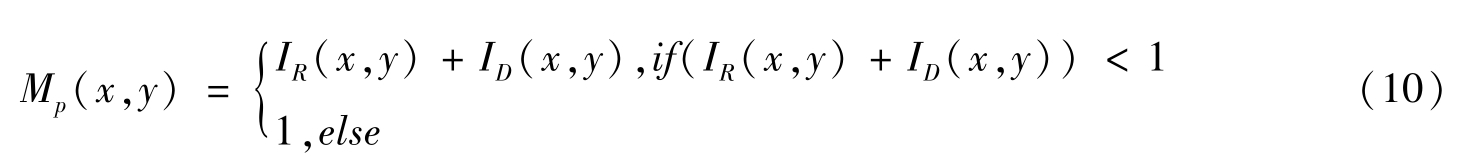
According to(10),
M
p
(
x
,
y
)
=I
R
(
x
,
y
)
+I
D
(
x
,
y
)when
I
D
(
x
,
y
)
<
1
-I
R
(
x
,
y
).It is easy to figure out that
I
D
(
x
,
y
)
<
1
-I
R
(
x
,
y
)when
x
∈
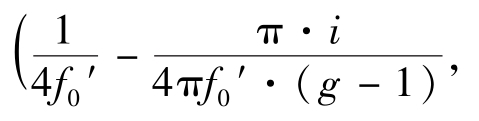
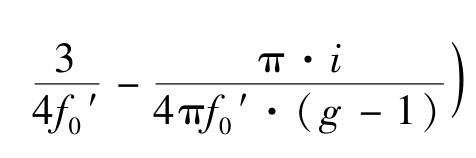 .According to Definition 1,the average grey-level is
.According to Definition 1,the average grey-level is
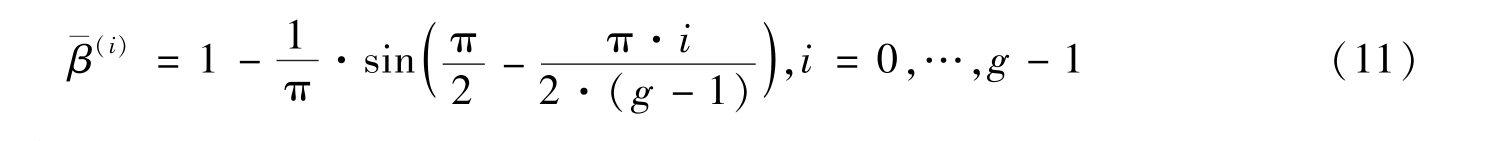
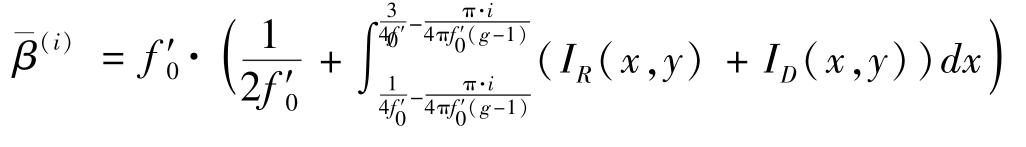
To prove(ii),when we superimpose two grey-scale images by Multiply mode,the moiré pattern is described by(4).According to Definition 1,the average grey-level is
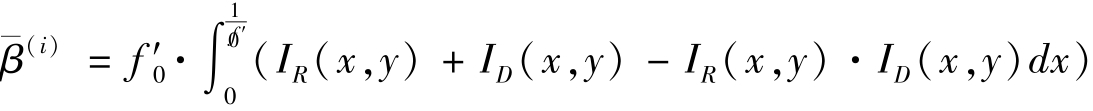
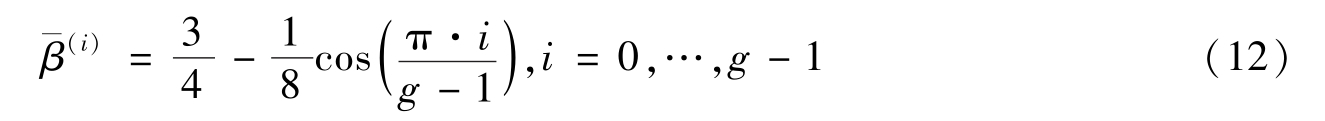
Corollary 1
.
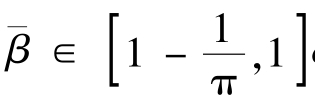 and average contrast between black and white is
and average contrast between black and white is
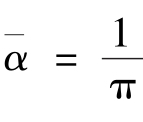 by
Sum mode
.
by
Sum mode
.
Proof
:
According to Theorem 2,
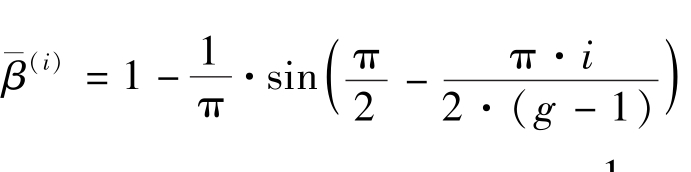 is amonotonic function.So the average grey-level of the 0th grey-level area(white)is1-
is amonotonic function.So the average grey-level of the 0th grey-level area(white)is1-
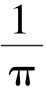 ,the average grey-level of the(g-1)th grey-level area(black)is 1.So
,the average grey-level of the(g-1)th grey-level area(black)is 1.So
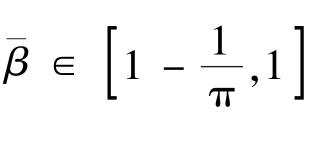 and average contrast between black and white is
and average contrast between black and white is
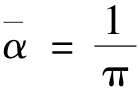 .
.
Corollary 2.
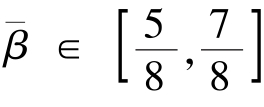 and average contrast between black and white is
and average contrast between black and white is
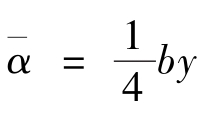 Multiplymode
.
Multiplymode
.
Proof
:
According to Theorem 2,
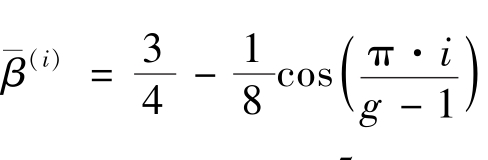 is amonotonic function.So the average grey-level of the 0th grey-level area(white)is
is amonotonic function.So the average grey-level of the 0th grey-level area(white)is
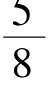 ,the average grey-level of the(
g
-1)th grey-level area(black)is
,the average grey-level of the(
g
-1)th grey-level area(black)is
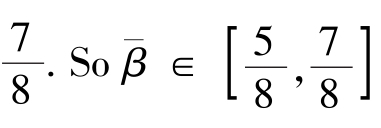 and average contrast between black and white is
and average contrast between black and white is
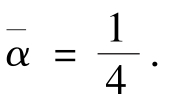
Theorem 2 shows the expected value of the average grey-levelwhen T is big enough.When T is not so big,the following table shows the comparisons of reconstruction qualitieswith different T and f 0 by Definition 1.
TABLEⅡ.RELATIONSHIP BETWEEN T , f 0 AND RECONSTRUCTION QUALITY BY SUM MODE.
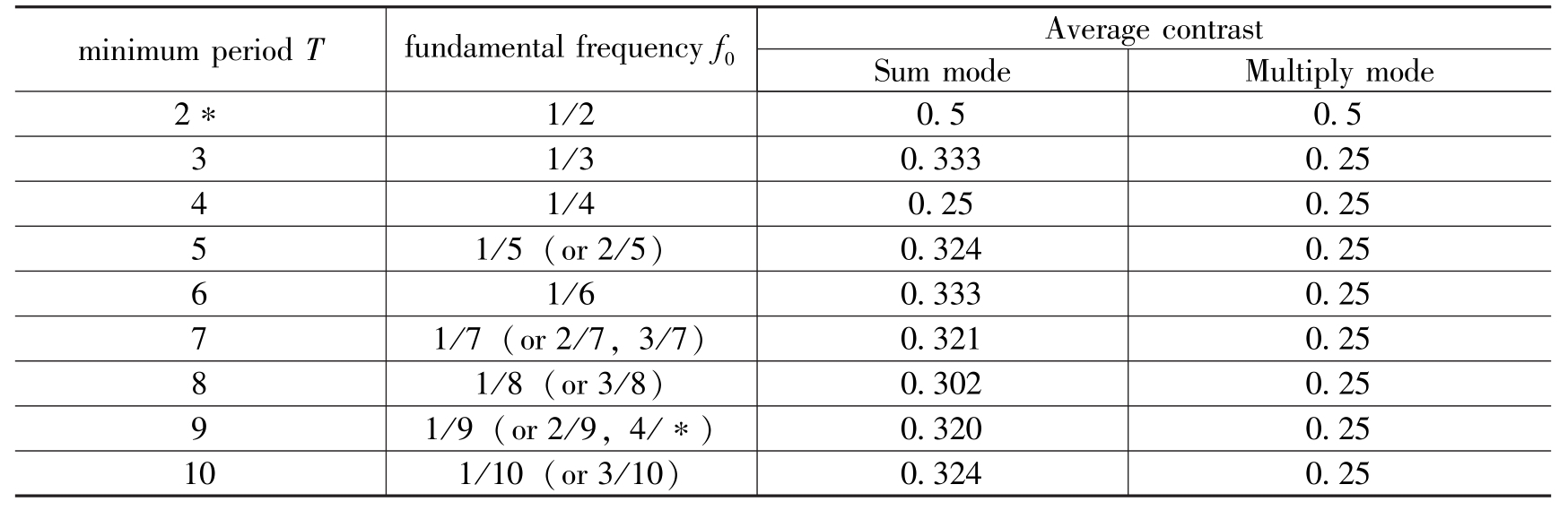
From the result,we observe that the reconstruction qualit is best when
f
0
=0.5 regardless of which superimposition model we use.It is because in this marked condition,
T
=2 is too small.When
T
becomes bigger,average contrast by Sum mode approaches
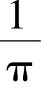 =0.318,which is same as Corollary 1.Average contrast approaches
=0.318,which is same as Corollary 1.Average contrast approaches
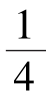 =0.25,which is same as Corollary 2.Also,when
=0.25,which is same as Corollary 2.Also,when
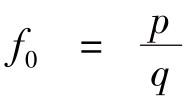 ,average contrast is same as when
,average contrast is same as when
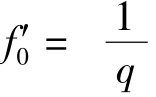 ,which is stated in Theorem 1.
,which is stated in Theorem 1.
In the above analysis,we propose some methods to calculate the reconstruction quality of the algorithm in[1].So these methods can give an objective evaluation of the reconstruction quality.
The basic generating equations and parameters are almost the same in[2-8],in this section we will show reconstruction qualitieswith differentλ.
Using(8)and(9)to be our generating equations,themoirépattern is described by
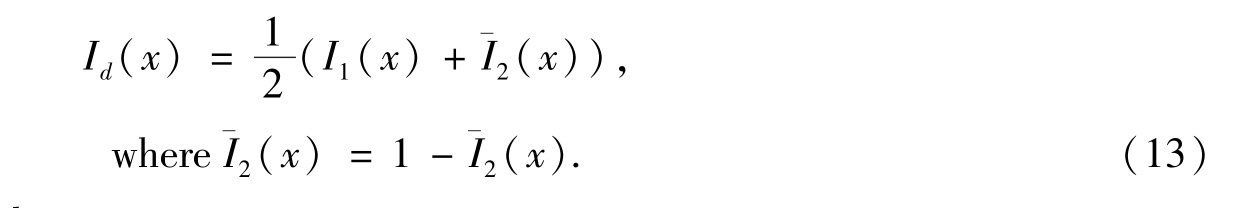
Nextwe can figure out the reconstruction quality by using Average contrast .
According to(8),the period of the pattern image isλ.The value of the
i
th grey-level
f
(
i
)
(
x
)cab bemapped into
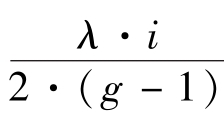 .According to Definition 1,the average grey-level is
.According to Definition 1,the average grey-level is
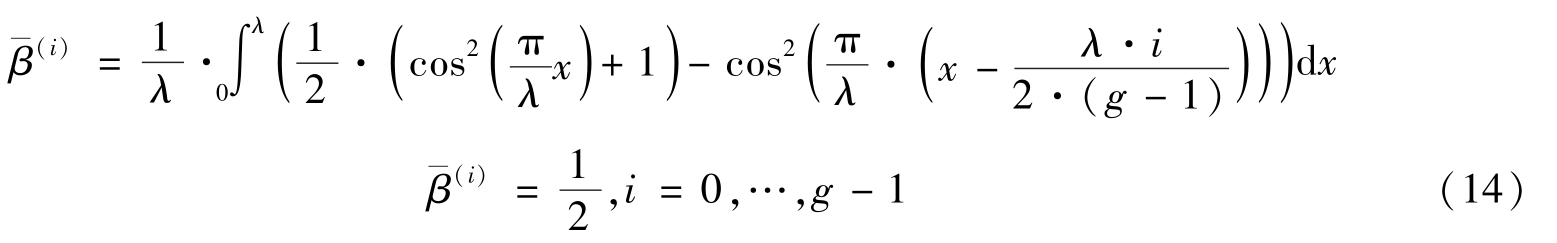
When
i
=0,namely
f
(
x
)
=
0,
I
d
(
x
)
=
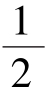 for any given
x
,However,when
i
≠0,
for any given
x
,However,when
i
≠0,
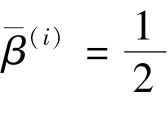 for any given
i
.So the reconstructed image can only be regarded as a binary image.
for any given
i
.So the reconstructed image can only be regarded as a binary image.
As
I
d
(
x
)=
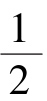 for any given
x
when
i
=0,average contrast between black and white can be redefine as
for any given
x
when
i
=0,average contrast between black and white can be redefine as
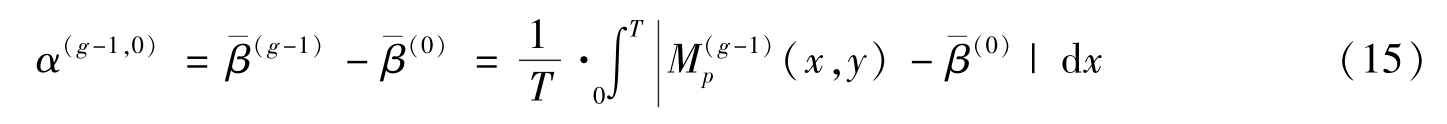
The following table shows the comparisons of reconstruction qualitieswhith different λ .
TABLEⅢ RELATIONSH IP BETWEEN A AND RECONSTRICION QUALITY IN[2-8]
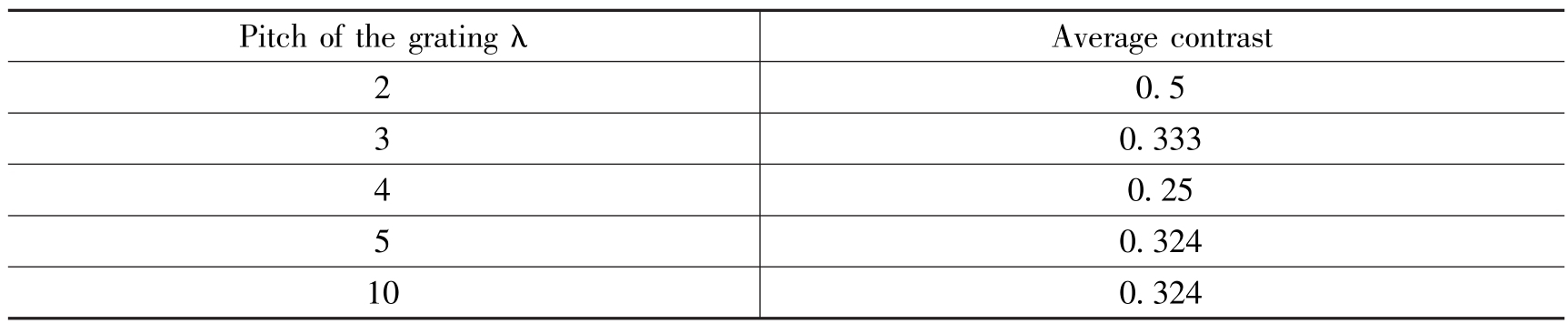
From the result,we can see that the reconstructed image can only be regarded as a binary image in[2-8].The reconstruction quality is bestwhenλ=2.
In this paper,we find the difference among reconstructed imageswith different parameters by image hiding algorithm based on moiré.We use average contrast to calculate the reconstruction quality and give its relationship with parameters of generating equations.Experimental results show that high reconstruction quality can be obtained by comparing different parameters.
This research was supported in part by the National Natural Science Foundation of China(Grant Nos.61170032,61272435,61373020,and 61379151),and in part by the Project of General Administration of press and publication of China(GAPP-ZDKJ-BQ/15-2).
[1]J.A.Muñoz-Rodríguez,R.Rodriguez-Vera.Image encryption based on moirépattern performed by computational algorithms.Optics Communications,2004,236(4)295-301.
[2]M.Ragulskis,A.Aleksa,L.Saunoriene.Improved algorithm for image encryption based on stochastic geometricmoiréand its application.Optics Communications,2007,273(2):370-378.
[3]M.Ragulskis,A.Aleksa.Image hiding based on time-averaging moiré.Optics Communications,2009,282(14)2752-2759.
[4]M.Ragulskis,A.Aleksa,Z.Navickas.Image hiding based on timeaveraged fringes produced by nonhannonic oscillations.Journal of Optics A:Pure and Applied Optics,2009,11(12):125411.
[5]M.Ragulskis,A.Aleksa,J.Ragulskiene.Image hiding based on circularmoiréfringes.WSEASTransactions on Mathematics,2010,9(2)90-99.
[6]E.Sakyte,R Palivonaite,A.Aleksa, et al .Image hiding based on near-optimalmoire gratings.Optics Communications,2011,284(16):3954-3964.
[7]R.Palivonaite,A.Aleksa,A.Paunksnis, et al .Image hiding in timeaveraged deformable moire gratings.Journal of Optics,2014,16(2):025401.
[8]V Petrauskiene,R.Palivonaite,A.Aleksa, et al .Dynamic visual cryptography based on chaotic oscil-lations.Communications in Nonlinear Science and Numerical Simulation,2014,19(1):112-120.
[9]Z.Wang,A.C.Bovik.Modern image quality assessment,Morgan&Claypool Publishers.
[10]S.Cimato,R.De Prisco,A.De Santis.Colored visual cryptography without color darkening.Theoretical Computer Science,2007,374(1):261-276.
[11]D.S.Wang,F.Yi,X.Li.Probabilistic visual secret sharing schemes for gray-scale imagesand color images.Information Sciences,2011,181(11)2189-2208.
[12]D.S.Wang,L.Dong,X.Li.Towards shift tolerant visual secret sharing schemes.IEEE Transactions on Information Forensics and Security,2011,6(2)323-337.